Remediating Agent Identities for Identity Admins and SOCs
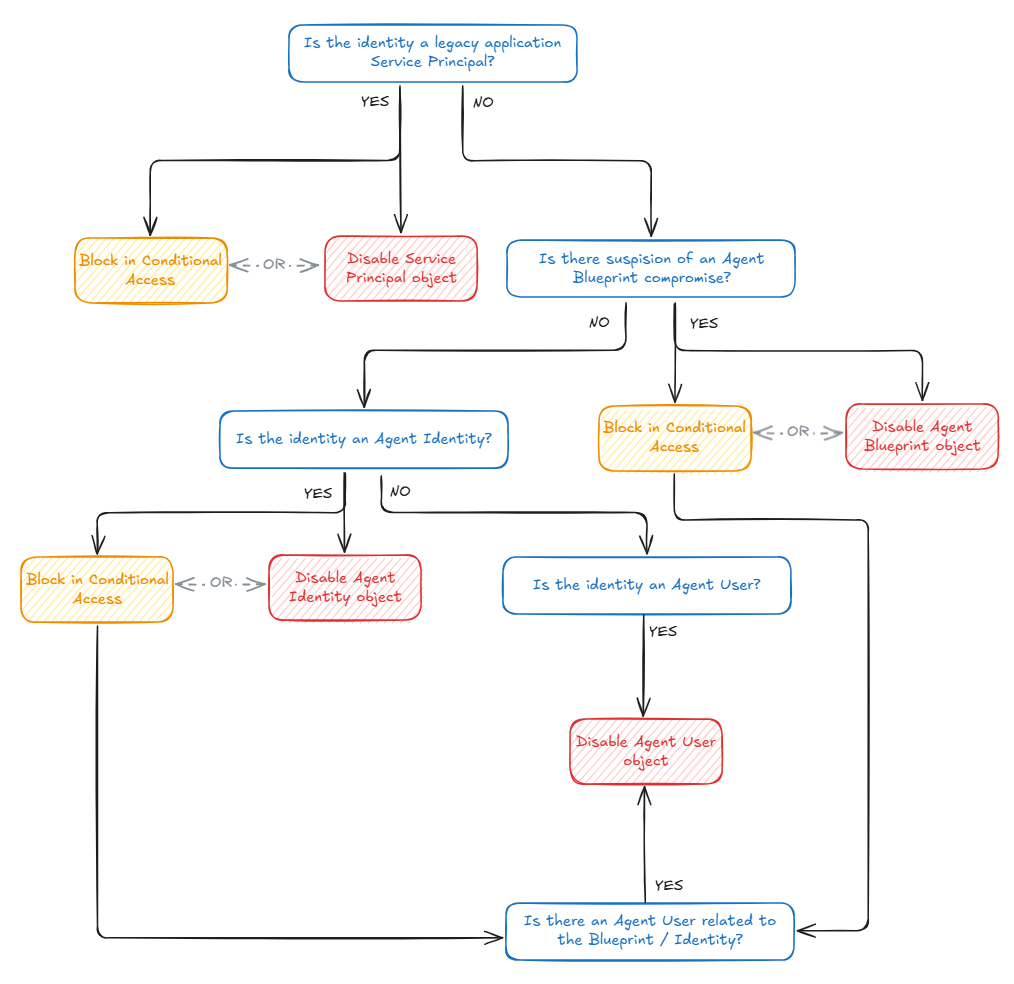
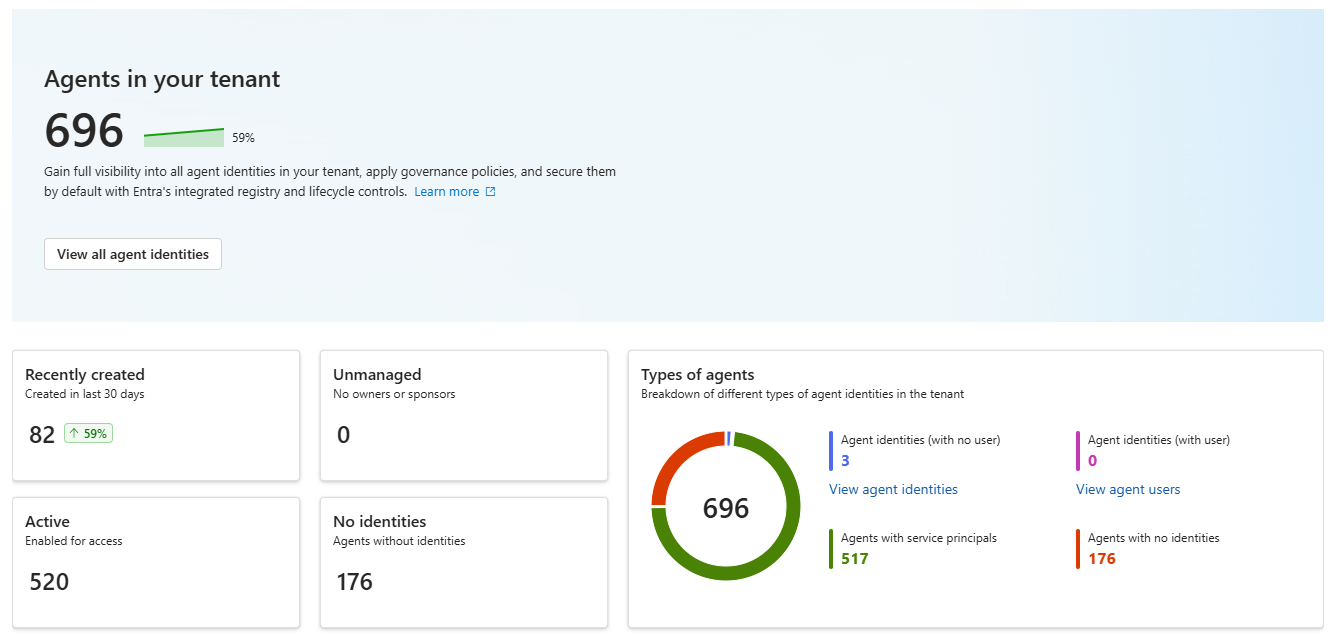
With Microsoft launching Agent ID at the end of 2025, a new kind of identities were born in Entra ID. These identities are specially built for dynamic requirements of AI Agents, and is therefore a completely now concept to understand for Identity Administrators. But more importantly, how is your organization going to respond if one of these new identities are compromised? We will go over it here, focussing specifically on how to remediate the identities linked to the agent.